Hashcat, básicamente, vendría a ser la versión "free" de PasswordsPro. Como ventajas les puedo comentar que en si es mucho más rápida que ésta (es multi-threading), soporta una gran cantidad diversa de hashes, y lo mejor, es gratuita y disponible para Windows / *nix. Adicionalmente existe una versión GUI para Windows. Más abajo también les dejo oclHashcat, lo mismo pero que utiliza el CPU de Nvidia (CUDA) o ATI, según se disponga (mucho más veloz).
Características (Inglés) (Hashcat):
* Free
* Multi-Threaded
* Multi-Hash
* Linux & Windows native binaries
* Fastest cpu-based multihash cracker
* SSE2 accelerated
* All Attack-Modes except Brute-Force and Permutation can be extended by Hybrid-Attack rules
* Very fast Hybrid-Attack engine
* Rules mostly compatible with JTR and PasswordsPro
* Possible to resume or limit session
* Automatically recognizes recovered hashes from outfile at startup
* Can automatically generate random rules for Hybrid-Attack
* Load hashlist with more than 3 million hashes of any type at once
* Load saltlist from external file and then use them in a Brute-Force Attack variant
* Able to work in an distributed environment
* Specify multiple wordlists and also multiple directories of wordlists
* Number of threads can be configured
* Threads run on lowest priority
* 33+ Algorithms implemented with performance in mind
* ... and much more
Características (Inglés) (oclHashcat):
# Free
# Multi-GPU
# Multi-Hash
# Linux & Windows native binaries
# Uses OpenCL
# Fastest multihash MD5 cracker on NVidia cards
# Fastest multihash MD5 cracker on ATI 5xxx cards
# Supports wordlists (not limited to Brute-Force / Mask-Attack)
# Can mix wordlists with Mask-Attack to emulate Hybrid-Attacks
# Runs very cautious, you can still watch movies while cracking
# Number of workload can be configured (like -n in hashcat)
# Supports pause / resume
# Supports huge numbers of hashes (4 million and more)
# Able to work in a distributed environment
# Includes hashcats entire rule engine to modify wordlists on start
(Hashcat) soporta:
* MD5
* md5($pass.$salt)
* md5($salt.$pass)
* md5(md5($pass))
* md5(md5(md5($pass)))
* md5(md5($pass).$salt)
* md5(md5($salt).$pass)
* md5($salt.md5($pass))
* md5($salt.$pass.$salt)
* md5(md5($salt).md5($pass))
* md5(md5($pass).md5($salt))
* md5($salt.md5($salt.$pass))
* md5($salt.md5($pass.$salt))
* md5($username.0.$pass)
* md5(strtoupper(md5($pass)))
* SHA1
* sha1($pass.$salt)
* sha1($salt.$pass)
* sha1(sha1($pass))
* sha1(sha1(sha1($pass)))
* sha1(strtolower($username).$pass)
* MySQL
* MySQL4.1/MySQL5
* MD5(Wordpress)
* MD5(phpBB3)
* MD5(Unix)
* SHA-1(Base64)
* SSHA-1(Base64)
* SHA-1(Django)
* MD4
* NTLM
* Domain Cached Credentials
* MD5(Chap)
* MSSQL
(oclHashcat) soporta:
* MD5
* md5(md5($pass))
* md5(md5($pass).$salt)
* MD4
* NTLM
Screenshots:
Hashcat Client (Linux-Terminal):

Hashcat-GUI (Windows):

Comparación de velocidad (Hashcat):

oclHashcat (Hashcat para CUDA / ATI):
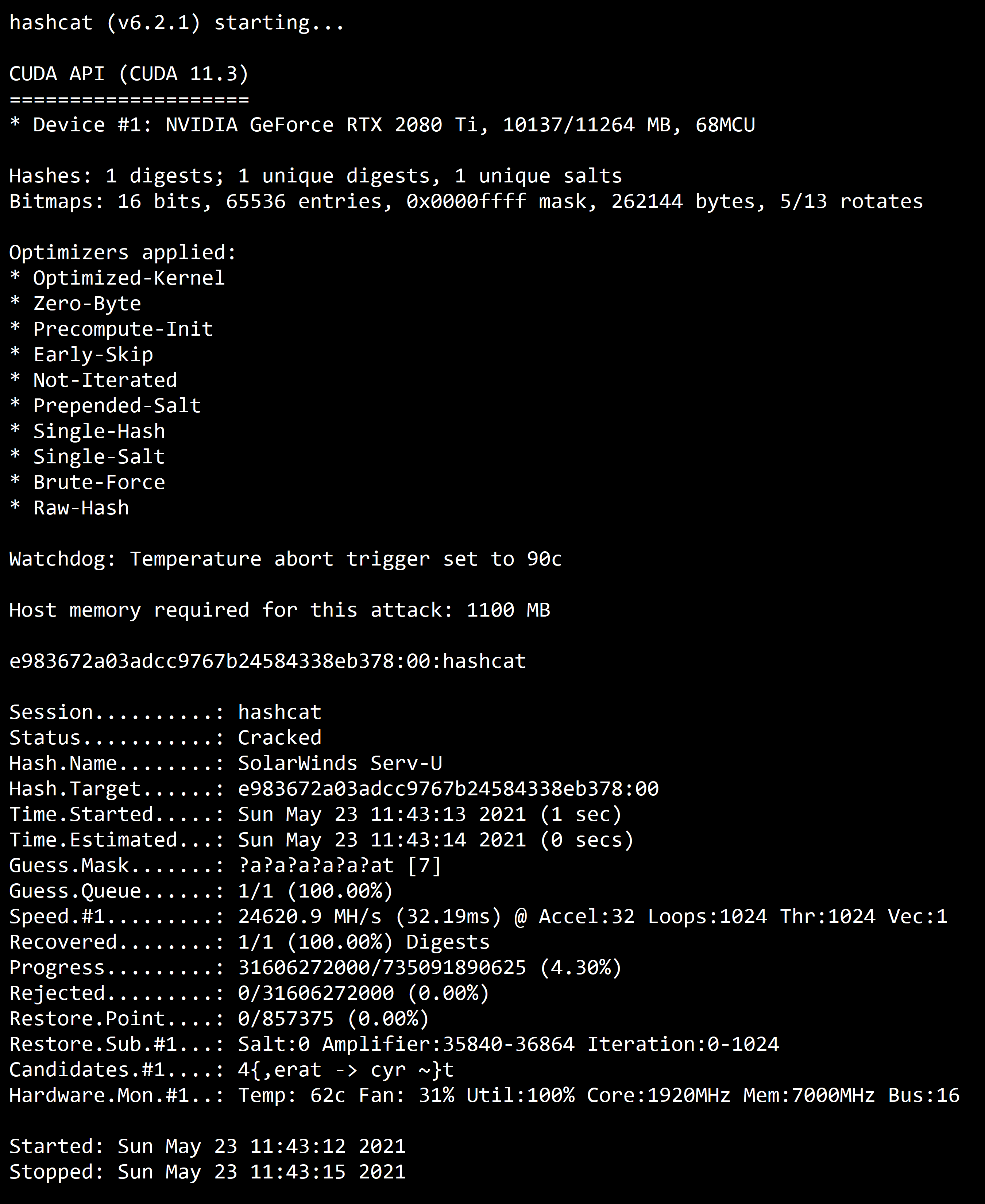
Comparación de velocidad (oclHashcat):

Download (Hashcat) (Terminal Version - *nix / Windows):
http://hashcat.net/files/hashcat-0.34.rar
Download (Hashcat) (GUI Version - Windows):
http://hashcat.net/files/hashcat-gui-0.2.433.rar
Download (oclHashcat) (Terminal Version - *nix / Windows):
http://hashcat.net/files/oclHashcat-0.18.rar
Página Oficial:
http://hashcat.net/hashcat/
Fuente: http://foro.latinohack.com/





0 Notaciones:
Publicar un comentario